Difference between revisions of "Security Group"
From All n One's bxp software Wixi
Philip Lacey (talk | contribs) m (→Security) |
Philip Lacey (talk | contribs) m (→Security) |
||
| Line 43: | Line 43: | ||
== Security == | == Security == | ||
| − | + | This feature is fully described here [[Security_Groups_for_managing_security]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | This | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
==HRM (Human Resources Management)== | ==HRM (Human Resources Management)== | ||
Latest revision as of 20:15, 16 March 2018
1 Overview
A Security Group is a leaf in the Organogram of a company Organogram_with_Group_Profiling
A Security Group allows you to specify a business unit and then perform a number of actions with that group.
Often Groups start at a broad level all the way down to teams of 1 to 4 people.
Groups are also used to create logical units of people associated with the business or clients who have log ins to your bxp system.
2 Attached data
It is possible to store a lot of information with a Security Group.
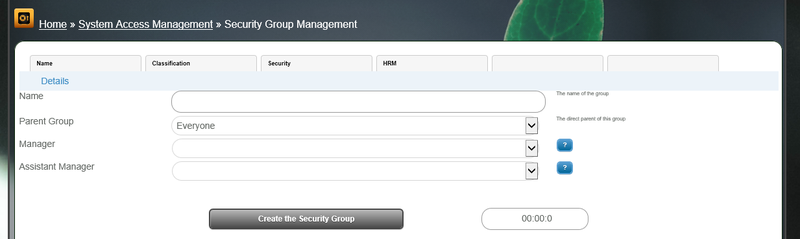
2.1 Details
- Name : This is how the group will be represented through the system
- Parent Group : All first level entries will belong to the "Everyone" group and then spread outwards from there.
- Manager : Is a bxp user account primarily responsible for the group. This allows HR functions to be more easily managed.
- Assistant Manager : Is a bxp user account which has the same permissions to perform functions as the manager for HR related updates.
2.2 Classification
- Sort Order : By default the system will sort alphabetically on name but a custom sort order can be applied.
- Icon : It is possible to specify an image with the security group. If you use a number one of the system default icons will be displayed or you can use a URL to specify the image
- TOM - FTE : Target Operating Model - Full Time Equivalence is a float point number used in a TOM model. Human_Resources_Management_-_Target_Operating_Model_(TOM)
- TOM - Roles : Another TOM model. Roles are added as ID-X,ID-X Where ID is the ID of the role and X is the FTE amount of that role required.
2.3 Security
This feature is fully described here Security_Groups_for_managing_security
2.4 HRM (Human Resources Management)
- ESS Details : Allows for a custom layout for dealing with people from this Security Group when managing them through the Security Group Manager section in the HR module.
- ESS JavaSript : The JavaScript for the above ESS Details
- HR fields : When listing users in this Security Group in HR reports this overriding list of HR fields can be applied.
3 Use of Security Groups
3.1 To view your current structure
Main Menu > System Access Management > Security Group Management > Organogram with Group Profiling >
Each of the branches are clickable to allow you to review the users in that branch of the tree.
The display will also show all the branches and their members.
3.2 To add a Security Group / Branch
Main Menu > System Access Management > Security Group Management > Security Group - Add >
- Give your security group / branch a unique name.
- Choose the parent to attach it to
Below is a display of the current structure to serve as a reminder.
3.3 Profile a User
If you want to see what Security Groups / Branches a user is in the this report makes it easy to see.
Main Menu > System Access Management > Security Group Management > Profile a User >
3.4 To associate users with a Security Group / Branch
Main Menu > System Access Management > Security Group Management > Add User to a Security Group >
- Choose the group
- Choose the users
- Click "Continue"
4 Security Groups for Forms
There are statistic reports for forms in the Data Profiling that need a Security Group allocated to the form. Form access is managed on a user by user basis for the most granular level control possible. However for quick group reporting a security group can be associated with the form. This association does not change form content access permissions.