Difference between revisions of "Reporting - Security Reports"
From All n One's bxp software Wixi
Philip Lacey (talk | contribs) (→Web applications) |
Philip Lacey (talk | contribs) (→Web applications) |
||
| Line 122: | Line 122: | ||
| − | All n One generate security reviews of client applications on behalf of the client as a paid service. [[ | + | All n One generate security reviews of client applications on behalf of the client as a paid service. [[Bxp_-_Client_Security_Report]] These reports are delivery back to the client through the bxp Client Dashboard. [[bxp_Client_Dashboard_Report]] |
Latest revision as of 15:29, 31 December 2015
Contents
1 Overview
The primary interface security reports are available through Main Menu > System Access Management > Security Reports
These reports are collectively referred to as Security - Application Level reports.
They can be viewed under a number of categories.
2 Report Types
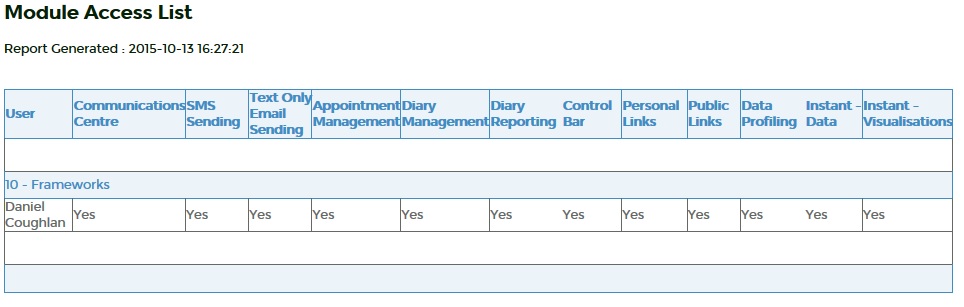
2.1 Module Access Report
The module access report shows what modules a user has access to in the system.
Main Menu > System Access Management > Security Reports > Security - Group User - Access Report
The first step is to limit by user, if no user is selected all users will be shown.
The next step is to limit by module and section.
Select the module and sections that are required and submit the page.
The page lists off all users and modules selected, and if the user has access to them.
2.2 Password Attacks
Passwords and their maintenance is a responsibility of the bxp client. There are a number of reports to facilitate easier user management.
Main Menu > System Access Management > Security Reports >
- Security - Password Strength Security_-_Password_Strength_Report
- Login Report - Last Login Security_-_Last_Login_Report
- Login Report - All Logins
- Login Report - Failed Logins
- Login Report - Failed Logins - IP Restricted
2.3 Maintaining Access
Ensuring that bxp is available is a complex task when you consider is the Infrastructure, Network and Application are available.
The primary test is that the login page of your system is available https://ww3.allnone.ie/client/client_XXX/main/login.asp responds. The demo system can be used to ensure IP address restrictions are not being applied https://ww3.allnone.ie/client/client_express/main/login.asp
Where a system check is required, there is an engine available through the BEAPI for heartbeat checking. https://ww3.allnone.ie/client/client_xxx/cti/userCTI_Alive.asp It is also possible to use the Demo system for independent checking https://ww3.allnone.ie/client/client_express/cti/userCTI_Alive.asp
bxp has been 100% available since October 2008
Outages, security changes and information updates are available through the bxp Client Dashboard bxp_Client_Dashboard_Report
2.4 Reverse Engineering
The output of bxp is XHTML 1.0, CSS and JavaScript (including AJAX, JSON, jQuery and other JavaScript libraries). Client side rendered information is easily viewable. Server side code is written in Classic ASP and VBScript with DOS and VBScript scripting supporting server processes. Microsoft IIS Server maintains the security of not delivering server side code to the client browser.
Error messages generated from IIS are communicated in the form of Hamsters. Meet_the_Hamsters. A Hamster report is also available through the bxp_Client_Dashboard_Report for bxp client review and management.
At the bottom of every page is a "Debug Information" link. This link mirrors back to the user all the information their browser is transmitting for client side reverse engineering of browser output.
2.5 Stress Testing
Stress testing is performed internally on a client request basis. The results of stress tests are made available through the bxp Client Dashboard bxp_Client_Dashboard_Report
2.6 Vulnerability Analysis
The primary vulnerability at an application level for security is improper user account management. There are a number of mechanisms to support management of this area
Main Menu > System Access Management > Security Reports >
The primary report is Security - User Status Security_-_User_Status This provides an overview of all users, including individual users by department.
It is important to understand the difference between Function and Content Function_Vs._Content.
Function: This can be reviewed on a user by user basis using Main Menu > System Access Management > User Administration > Edit User - Security Details > Lookup the user > Select the user > It is possible to see what modules and sections are allocated to the user.
Content: This can be reviewed using Main Menu > System Access Management > Security Reports > Security - User Profile - By Lookup > Lookup the user > Select the user > which shows what content is available on a user by user basis.
If vast amounts of content are added or removed it is important for the bxp client to track these details. Main Menu > System Access Management > Security Reports > System Reports - System Profile provides a benchmark profile of the system.
There are various security events that occur in the system such as user adding, editing, etc. These are all audit-able through Main Menu > System Access Management > Security Reports > Security - System Event Audit Trail System_Access_Management_-_Security_-_System_Events_Audit_Trail
System level identified vulnerabilities are communicated the bxp Client Dashboard bxp_Client_Dashboard_Report
2.7 Web applications
All n One generate security reviews of client applications on behalf of the client as a paid service. Bxp_-_Client_Security_Report These reports are delivery back to the client through the bxp Client Dashboard. bxp_Client_Dashboard_Report