Bxp and Active Directory for Single Sign On (SSO)
Contents
1 Introduction
Often a client will want to save users the hassle of having to log into multiple systems. There is a mechanism called Single Sign On, where as the user logs into the machine, credentials are available to other solutions to save a log in process.
There is some set up to this process and this Wixi describes this process
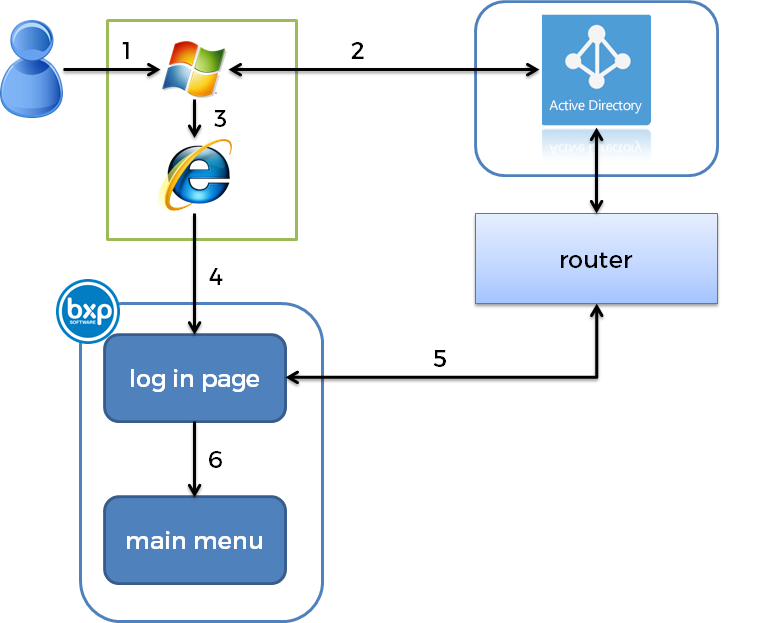
2 Process Overview
- A user logs into their machine using Windows
- Windows in the background chats to the Active Directory Domain Controller
- The validly logged in user opens up a browser
- The browser requests the login page within bxp. It also passes extra information in the Request Headers.
- bxp extracts the details from the header and communicates to the AD to identify the user
- Upon validating the user the user is logged into bxp
3 Server Setup
3.1 Setting up LDAPS
Active Directory is the primary security engine of Windows Server. Wikipedia Active Directory Microsoft Active Directory
The simplest way of interacting with the server for bxp is through LDAPS. [LDAPS]
Once you have a Windows Server set up with Active Directory and your users logging into a domain you can make the service available through a number of means.
- Configure LDAP settings
- Event ID 1220 — LDAP over SSL
- Enabling Secure LDAP on Windows Server 2008/2012 Domain Controllers
- LDAP over SSL (LDAPS) Certificate
- How to enable LDAP over SSL with a third-party certification authority
3.2 Securing your LDAPS server for use with bxp
Making your AD available to the public is a potential security risk. So there are a number of things you can do to shore up the risk.
Firstly, bxp will only connect with you from specific IP addresses. You can restrict access to your AD through your router to the bxp IP addresses
- 82.195.138.167
- 82.195.138.174
bxp starts an LDAP session by connecting to an LDAP server, called a Directory System Agent (DSA), by default on TCP and UDP port 389, or on port 636 for LDAPS.[8]
Global Catalog is available by default on ports 3268, and 3269 for LDAPS.
So restricting the firewall to only allow for the specific IPs, the specific ports and may those ports directly to the DC.
3.3 Testing your router configuration
So testing that your router configuration and LDAPS is working you can log into bxp and use a special page. Please change the client_demo to your system. This will allow you test domain, user and password tests.
https://ww3.allnone.ie/client/client_demo/main/userAD_Test1.asp
This page shows all of the available variables that are being passed to your web browser, The four variables at the top of the page, in the section Active Directory Variables will give you an idea of what the browser can see. If these four variables are blank you will not be able to use your browser for single sign on on its own. bxp does offer a file that can be give upon request that allows the use of single sign on, this file gets the required information and then passes to to a browser of your choosing.
4 Configuring bxp
4.1 What you can transmit from your network
The first important part is to see are the key header variables indicating domain login
https://ww3.allnone.ie/client/client_demo/main/userAD_Test2.asp
There are two primary pieces of information required in the header AUTH_USER and AUTH_PASSWORD.
- If AUTH_USER is blank, bxp will bounce to a login page
- If AUTH_USER is not blank, AUTH_PASSWORD is blank, bxp will bounce to a login page but pre-populate the user details
- If AUTH_USER is not blank, AUTH_PASSWORD is not blank, bxp will log the user in and continue to the main menu
4.2 Log in pages
There are three log in pages
- login.asp
- login2.asp
- loginad.asp
loginad.asp is the redirect page for failed AD log ins.
A system must use or not use Active Directory. There are configuration settings set at a system level which inform this system how to get in touch with the domain.
By default AD login will not be enabled, please contact support@allnone.ie or +353 1 429 4000 if you need to change these settings.